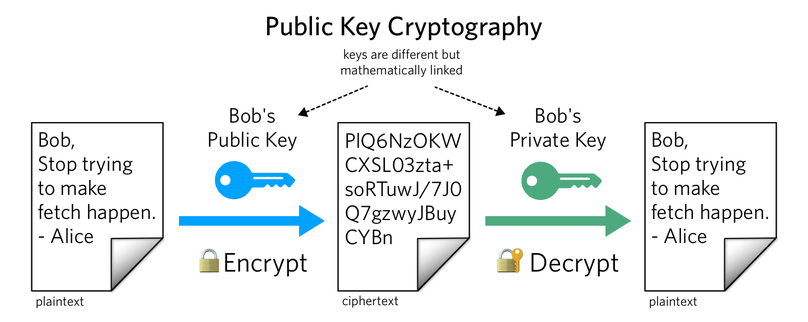
![PDF] Public Key Cryptosystem Technique Elliptic Curve Cryptography w ith Generator g for Image Encryption | Semantic Scholar PDF] Public Key Cryptosystem Technique Elliptic Curve Cryptography w ith Generator g for Image Encryption | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d4cb05572af274a00ca4425ffbf51df65279c370/3-Table2-1.png)
PDF] Public Key Cryptosystem Technique Elliptic Curve Cryptography w ith Generator g for Image Encryption | Semantic Scholar

Example of an embedded encryption scheme: real time image encryption... | Download Scientific Diagram
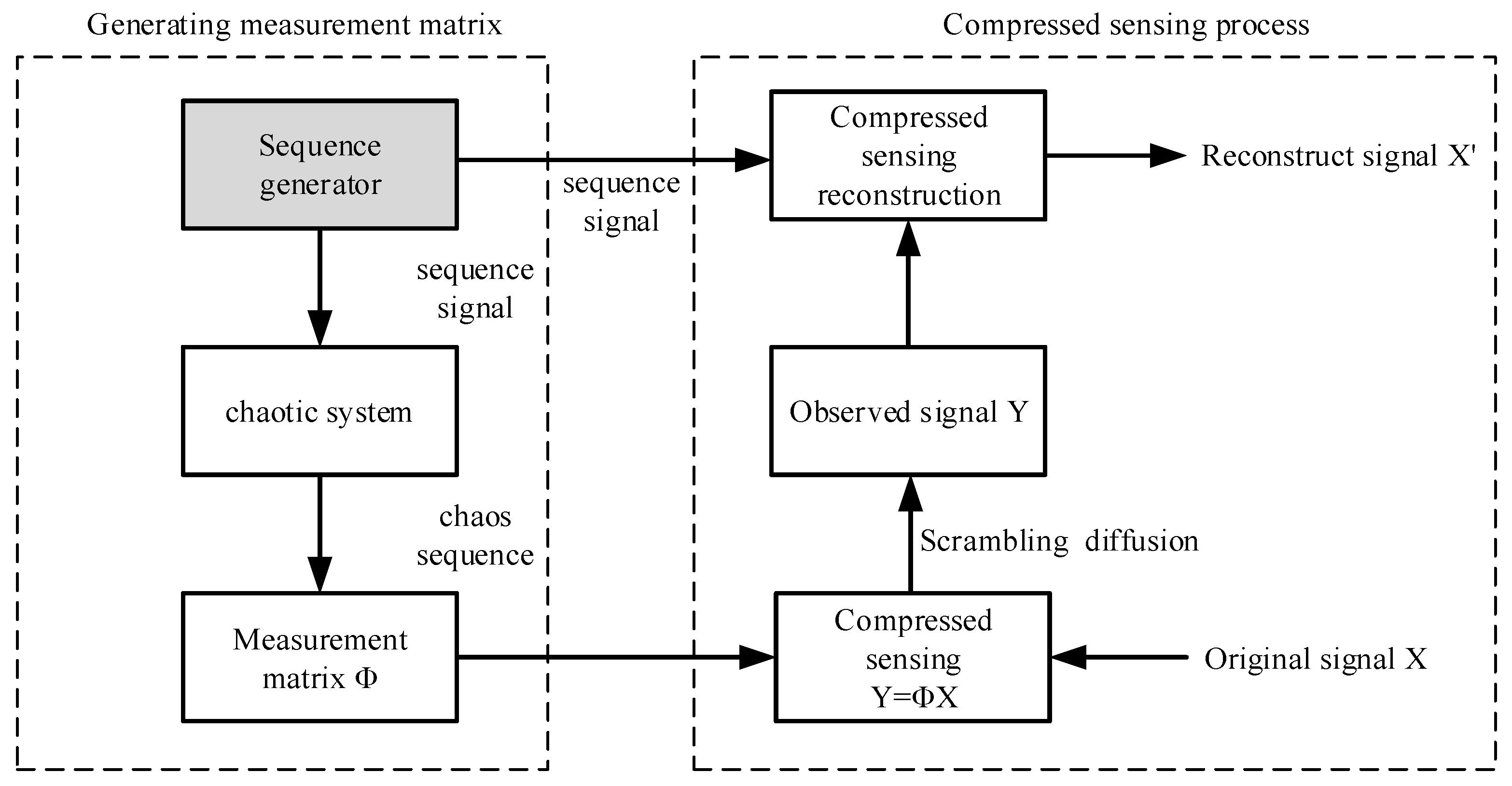
Entropy | Free Full-Text | Image Parallel Encryption Technology Based on Sequence Generator and Chaotic Measurement Matrix
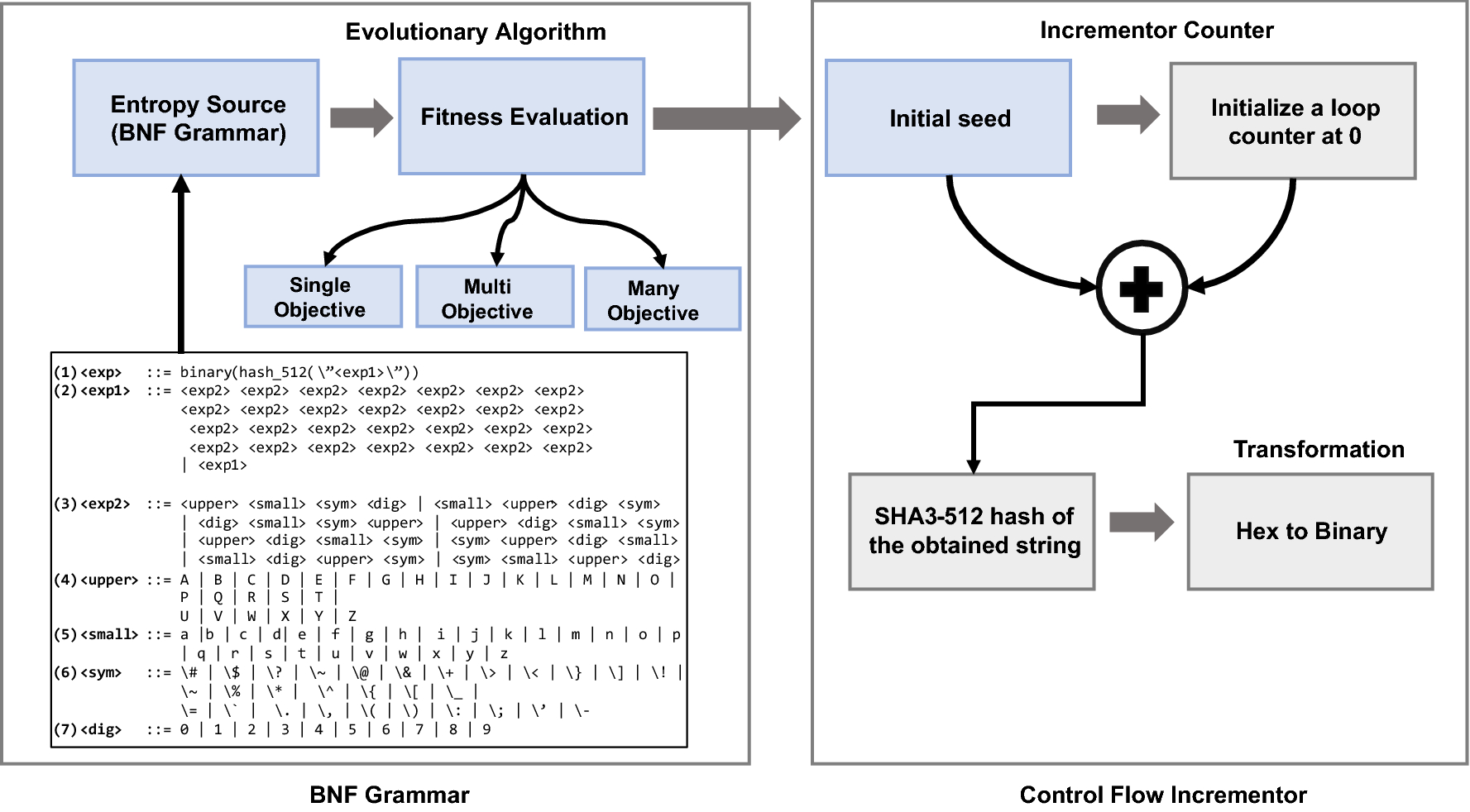
Design of a cryptographically secure pseudo random number generator with grammatical evolution | Scientific Reports
File:KG-83 Key Generator Encryption-Decryption Equipment - National Cryptologic Museum - DSC08014.JPG - Wikimedia Commons
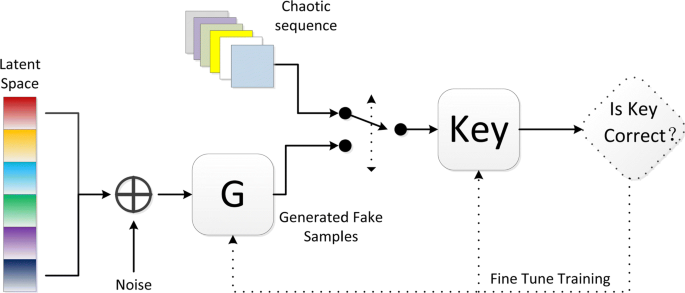
A novel image encryption algorithm based on least squares generative adversarial network random number generator | SpringerLink

CJMCU 608 Cryptographic Key Storage Random Number Generator Signature Encryption Decryption Module|encryption keys| - AliExpress